Internet connectivity is embedded in our society. Our digital transformation brings huge socio-economic benefits. With smart homes, smart transport, smart office space and smart cities, when it comes to our modern infrastructure, are we in fact, smart?
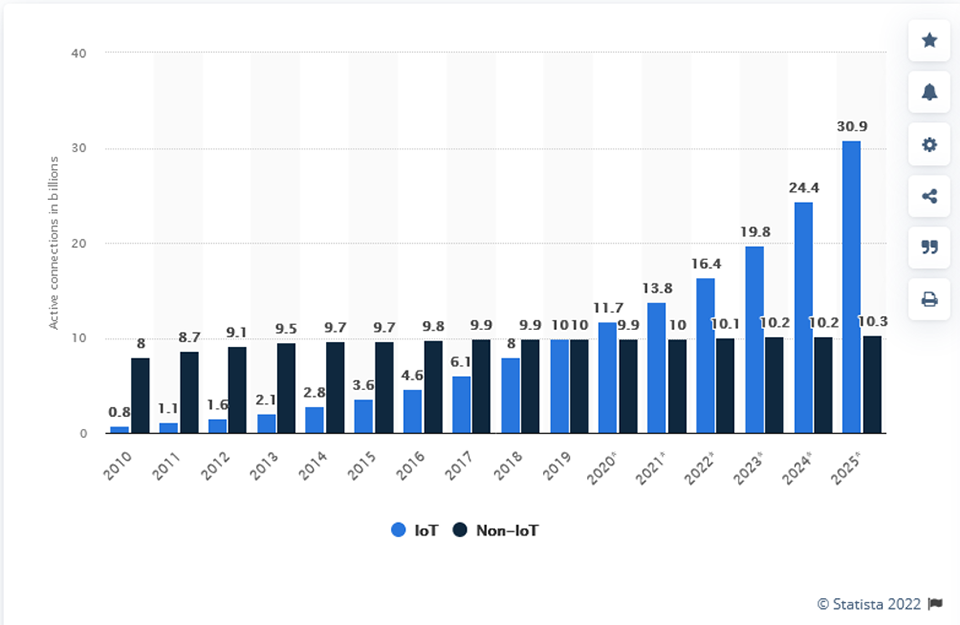
In 2019, there were an estimated 9.9 billion actively connected Internet of Things (IoT) devices globally**. By 2021, that figure grew substantially to 13.8 billion and continues to soar. Manufacturers find it increasingly beneficial to connect some of our most ordinary devices to the internet, profiting both financially and in terms of our valuable data.
Global Internet of Things spending is projected to reach US$ 1.1 trillion by 2023. The number of IoT devices is predicted to reach 3.9 billion by 2025.*
Statista. [May 2021]
It’s undeniable that the Internet of Things allows us to function in ways we never thought possible 20 years ago, but does this convenience and increased productivity come at a price? Is our personal and corporate data at far greater risk?
Our hyper-connectivity also means exposure to hyper-threats, which are bigger, faster and smarter. According to security provider, Kaspersky, IoT cyber-attacks are doubling year-on-year. In the first 6 months of 2021 there were 1.51 billion breaches of our Internet of Things devices; rising from 639 million in 2020.
Is the Internet of Things secure?
You might assume that we are automatically being protected; the tech companies have us covered, right?
Unfortunately not. As vendors jostle for position in a booming marketplace, expensive cybersecurity is given little thought; many smart devices are rushed to market with minimal or no built-in security. Our upgrade culture means that manufacturers are looking to sell us their latest gadget as soon as possible. But it isn’t only the tech companies profiting.
The lack of IoT security provides the perfect entry-point to access the wider network, invade your personal privacy or expose sensitive corporate data.
One device has a small amount of power but combine them to build an IoT army of millions, focused on a single target, and you’ve a powerful mechanism to launch large-scale Distributed Denial of Service (DDos) attack. Remotely controlled IoT botnets of hijacked tech, infected with malware, are designed to create maximum online disruption, server failure and data theft.
What are the hidden dangers of the Internet of Things?
Known vulnerabilities remain unpatched
In November 2021, IoT Security Foundation published their research following their analysis of hundreds of popular smart products. Four out of five manufacturers failed to provide a public method to report security vulnerabilities. Although this is a slight improvement on the previous year, the report authors describe progress of this basic cybersecurity practice as ‘glacial’.
Given that IoT best practice has been known since 2017 and ISO standards have been in place 2014, this is unacceptably low. Not only can vulnerabilities find their way into our products, with no communication channel, we have no way of reporting problems. Many devices cannot be updated at all, and if they can be, it might be difficult to do so.
Not all manufacturers should be tarred with the same brush, however. Good security practices are reported from the largest tech giants such as Apple, Samsung, Microsoft, Google etc… Nonetheless, consumers frequently purchase cheaper alternatives that appear the same, at least on the surface.
Users are often completely unaware that their device has been infected
Many devices are plug-in and play. Often the default password isn’t changed as it isn’t required after initial set up. A significant number of devices never receive any notifications to update the software. This leaves millions of devices whose users are simply unaware of the risk or the need for IoT cybersecurity.
Now a cultural norm, many people don’t think twice about giving up personal data for minimal benefit. With little thought, we download productively tools, ecommerce apps, games… That face-swapping app is pretty funny, but is it worth giving up your data for? We often click-through inconvenient permissions pop-ups on websites or app stores without even stopping to read them, but what use are technical security measures, if we no longer even notice them?
The cyber-criminals are keen to exploit our complacency. At the end of the day, no one is even going to notice if their toothbrush is being used in an IoT botnet.
There’s data in them there e-waste hills mountains
Laptops, desktops or servers are no longer the only devices that store our private data – the IoT includes office printers, copiers, security cameras, and even company car media consoles. Remote and hybrid working has also seen a rise in ‘bring your own device’ use, such as smartwatches – a common BYOD. It’s worth noting that wearables store as much data as smartphones and can be easily hacked.
More and more e-waste is generated every year as devices are upgraded every 12 -24 months. Many businesses simply write off the asset, assuming they are worth next to nothing, missing the opportunity to sell redundant IT assets. Assets are slung in office drawers or worse, in the general bin with no consideration of the information on the device.
One of the most widespread myths is that the factory-reset completely wipes a device – it doesn’t. Without total data erasure, you are also failing to protect company data, which could lead to serious legal and data security issues in the event of a data breach.

How can the Internet of Things cybersecurity be improved?
Legislation
The positive news is that manufacturers are soon to be held accountable for the Internet of Things cybersecurity.
The European Commission has adopted new cybersecurity rules for all types of internet–enabled devices. Crucially, the EU Cybersecurity Act enforces security by design and producers will have to include new features to prevent unauthorised access, exchange of sensitive data and the use of the devices in DDos attacks. Having recently come into force, manufacturers have 30 months to adapt.
There are positive steps forward across the pond, too. President Trump signed a new Internet of Things Cybersecurity Improvement Act for U.S government equipment in 2020. There is hope it will be expanded to include the entire IoT market.
That said, even if every Internet of things device built from now on has in-built security, there’s still vast numbers of devices out there without it, creating immense number of insecure end-points. Whether data is moving or at stationary, when it comes to Internet of Things security, all data should be encrypted, wherever possible.
Increase consumer awareness
Whilst government intervention is vital, one important factor should not be overlooked – the users.
ENISA, the European Union Agency for Network and Information Security, highlights the need for ‘electronic common sense’. In the same way that you instinctively look both ways when crossing a road, people need to be ‘trained’ to live in the electronic world intuitively.
Consumers can demand greater security from tech manufacturers, but how do you demand protection if you are unaware of the threat? Could more educated users help prevent cyber-attacks? When it comes to your business, regular employee training should form part of your IoT cybersecurity plan.
Dispose responsibly
When it comes to secure IT asset disposal of our smart devices, businesses need to exercise the same level of caution that they would any end-of-life IT asset. The IoT must be included in your IT asset disposal policy with all redundant IT equipment undergoing professional data erasure through your ITAD partner.
Environmentally friendly ITAD will provide a residual value return as many components can be used in the remanufacturing process and you’ll be contributing to the circular economy too.

Smart city and communication network concept. 5G. LPWA (Low Power Wide Area). Wireless communication.
The ever-increasing IoT must be futureproofed to prevent increasingly prevalent and catastrophic attacks. Government legislation will go a long way in ensuring responsible manufacture of our devices, protecting our privacy as individuals and our businesses from crippling cyber-attacks and data beaches.
However, despite incoming regulations, we must also take personal responsibility. Busy CISO’s and CIO’s must not overlook the multiple end-points of these increasing familiar, everyday devices. Given the number of active insecure devices, a zero-trust approach to all devices should be taken. Internet of Things security, employee training and professional data destruction must form part of your corporate cybersecurity strategy to prevent potentially catastrophic IoT-related cyber-attacks.
We innately turn to our internet-enabled devices, and it must become just as instinctive to prioritise our personal or professional cybersecurity.
Helping to prevent data governance issues, tier1 provide comprehensive data destruction services, including mobile device recycling and IT asset disposal. Our business support services ensures that your organisation meets the EU and UK GDPR data destruction requirements – providing you with a full ITAD chain of custody and an IT asset disposal accreditation for every end of life IT asset.
Find out more about the importance of asset disposal and our data wiping services – contact us on 0161 777 1000 or visit tier1.com
*PurpleSec, **esecurity planet, ^Statista
Resources.
ENISA, Zdnet, Tech Republic, Simplilearn. Trend Micro, Eu Observer, IT Goverance, IOT World Today, eSecurity Planet, Hobi, Proton Data, Option3, Purple Sec, Statista, Kaspersky,



